Technology and innovations often bring heated debates between its staunch supporters and critics who express their viewpoints on the effect of such innovations on humankind. Presently, the entire world is debating the impact of Artificial Intelligence (AI) and its long-term implications on society and humanity. AI in Cybersecurity, the threat intelligence has exponentially evolved to pass through tight security protocols without setting off the alarms.
Organizations across the world is embracing AI-driven solutions to be frontrunners in their respective domains. The arena of Cybersecurity which has the paramount importance of securing the digital infrastructure of every business in this interwoven world is no exception. The role of AI in Cybersecurity is at the forefront and organizations are exploring how AI-driven solutions help build robust cybersecurity infrastructures. Moreover, organizations face the challenges of AI/Cybersecurity conundrum as adversaries (malicious users) will also use AI technologies to penetrate security vulnerabilities.
According to IBM’s Cost of Data Breach Report-2023, organizations that employ AI-driven security and automation incur an average cost of $3.60 million on a data breach which is $1.76 million less than breaches at organizations that do not use AI-based security and automation capabilities. This means we have a 39.3% difference in average breach cost between companies embracing AI and automation and those not using it.
This blog comprehensively discusses the benefits of AI in cybersecurity, the future of threat intelligence, and examples of AI tools that are transforming the landscape of the cybersecurity arena.
Role of Artificial Intelligence in Cybersecurity
Understanding the Role of AI in Cybersecurity
Artificial Intelligence (AI) has been a buzzword in both the technology arena and other areas of business for quite some time. AI has evolved since its inception and today we have subsets within this domain called Machine Learning (ML), Deep Learning (DL), and Natural Language Processing (NLP).
These interwoven fields have a direct impact on how futuristic cybersecurity looks.
• AI as an overall discipline plays a critical role in automating processes, detecting anomalies, and enhancing threat detection and responses.
• ML, a subset of AI enables cybersecurity professionals to analyze historical data to identify patterns and make predictions.
• DL models can enhance malware detection, network traffic analysis, and threat classification
• Finally, NLP helps analyze text-based data (logs, emails, social media) for threat intelligence.
Also, it can do Sentiment analysis to detect malicious intent in communications. Overall, AI and its subfields are increasingly employed in building modern-day cybersecurity solutions.
Applications or Examples of AI in Cybersecurity

AI has a multi-faceted role in assisting Cybersecurity systems with its capabilities like pattern recognition and continuous learning. AI systems can analyze logs, comprehend source codes, predict threats, and analyze, or exploit vulnerabilities.
Broad application of AI in Cybersecurity or the latest developments in Cybersecurity AI can be classified under two sections
- Threat Detection Applications
- Decision-Making Applications
Typical Use Cases or Applications of AI in Cybersecurity
Use Case 1: Anomaly Detection
AI/ML algorithms imbibe pattern recognition capabilities aptly suited for anomaly detection in IT systems. They can detect aberrations or deviations from the normal behavior of systems and alert the cybersecurity professionals to take necessary steps. In addition, these algorithms can also identify user behavioral patterns like accidental data leaking or exfiltration and alert the respective authorities.
Technically anomaly detection means identifying unusual or rare patterns in system logs, traffic, or data. A meticulously trained ML system can spot such potentially harmful outliers. Normally such systems are implemented using real-time monitoring and alerting. Often statistical analysis is used for continuous monitoring of system behavior and actions. In case of any aberration or rare actions, an alert is generated.
In addition to recognizing anomalies, AI/ML can categorize such behavior into different groups. This process of subdividing deviations into different groups assists in assigning priority levels. By assigning priority numbers to anomalies, cybersecurity professionals can focus on more dangerous vulnerabilities without being caught in “alert-fatigue”, a tricky situation where professionals get tired of monitoring “trivial” alerts continuously.
Use Case 2: Threat Detection Intelligence
The next use case is Threat Intelligence. AI/ML-driven cybersecurity systems can easily accomplish anomaly detection and take proactive steps to predict future events. Cyber Threat Intelligence (CTI) is a mechanism for gathering information about cybersecurity attacks and events. Its goal is to ensure the cybersecurity teams can anticipate any possible threats to your organization well in advance. In simple words, cyber intelligence threat provides a proactive dimension to an otherwise reactive defense mechanism.
CTI also assists incident response teams in dealing with existing attacks by making them understand the intricacies of the threats.
Additionally, the traditional approach of collecting, organizing, and analyzing data by security professionals is said goodbye, through the automation of mundane tasks. Now security professionals can focus on strategic and decision-making activities.
Use Case 3: Automated Code Scanning
Preventing vulnerabilities with AI-driven automated code scanning is the next use case.
Traditionally Static Application Security Testing (SAST) is used by software developers for code scanning. This process helps in tracking the data flow and detecting common pitfalls. The main limitation of this analysis is that it can lead to many false positives and requires human intervention to validate them manually.
Integrating AI/ML systems with the code-scanning process adds value as it can learn and understand the context of the findings in the code base, reducing the number of false positives and false negatives. This AI enablement saves time and money by releasing human resources to focus on complex strategies and decision-making activities.
Use case 4: Automated Discovery of Vulnerabilities
The code reviews are not the end of software testing. Developers or Testers have to test for common attacks against a running application through Dynamic Application Security Testing (DAST). DAST requires ramp-up and consumes time as users need to understand attack types and replicate those attacks using DAST tools.
Integrating AI/ML with DAST platforms as plugins enables developers to automate the code-scanning process. Importantly, they can focus on building comprehensive penetration testing which demands human intervention due to its complex nature.
Use Case 5: AI-assisted Penetration Testing and Ethical Hacking
Though in the previous use case, we mentioned that Penetration Testing largely requires human expertise to design or simulate a cyber-attack, it does not mean utilizing AI/ML tools is ruled out.
AI/ML tools can help cyber experts build efficient and scalable solutions. It enables faster testing of a huge volume of data, exploits vulnerabilities faster, and assists human experts with the knowledge of finding novel cyber attacks and systems to which they have little or no exposure.
Use Case 6: Data Loss Protection
Data Loss Protection (DLP) comprises a set of policies and procedures to protect sensitive information like Personally Identifiable Information (PII), Intellectual Property (IP), financial data, and credentials from unauthorized access.
AI/ML tools can act as core enablers of the DLP process with unique capabilities:
- With Natural Language Processing (NLP) capabilities, analyzing emails and other documents to identify and classify sensitive information with precision is easier
- AI/ML tools can recognize sensitive information embedded in images and non-text objects
- User and Entity Behavior Analytics (UEBA) is handy in detecting unusual behavior of users and entities, thus detecting unauthorized access or data filtration.
Classifying and monitoring large data sets is a herculean task for human experts. Artificial intelligence and machine learning tools can automate these activities and with their continuous learning and adaptable traits. AI in cybersecurity can easily identify emerging risks and dynamically changing attack vectors.
Use Case 7: Identity and Access Management
Identity and Access Management (IAM) consists of user authentication, authorization, and active monitoring to ensure the right access or privileges are given to the right person. The entire process of IAM can become cumbersome and tedious if monitored manually by a human resource. AI tools can make life easier for administrators with automation, adaptability, and intelligence traits that can manage processes with advanced data analysis capabilities. AI technology employs behavioral biometrics so that any aberration in user behavior can immediately prompt Multi-Factor Authentication.
Access to vast data banks and advanced data analytics abilities make AI-driven IAM a better bet.
Benefits of AI in Cybersecurity
A TechRepublic report says, every day, a midsized company receives around 200,000 alerts of cyber discrepancy. Handling such a voluminous task is next to impossible. So, organizations are relying on A for cybersecurity defense against such dynamically emerging attacks. Here we have identified the salient benefits of using AI-driven Cybersecurity measures:
AI Detects Unknown and Novel Threats
Hackers are rampantly changing their tactics and it is an uphill task for any organization to identify all types of potential threats. AI/ML-driven tools can be your ally in effectively detecting and thwarting novel and unknown cyberattacks.
Voluminous Data Handling Capabilities of AI
In modern-day organizations, a huge amount of data gets generated and it is a herculean task for cybersecurity professionals to manually monitor all incidences and identify potential threats. Employing AI for cybersecurity tools can identify hidden threats, streamline threat detection process, and enhance protection.
AI tools handle time-consuming tasks swiftly by detecting false positives and identifying non-threatening activities relieving human resources to focus on critical tasks.
AI’s Unrivalled Learning Abilities
AI is a continuous learner who never gets tired! This trait of AI tools makes it challenging for hackers to outsmart them. AI employs deep learning techniques to analyze deviations in network behavior and can swiftly counter potential threats to ensure robust security mechanisms.
AI/ML-based cybersecurity systems can prioritize types of attacks and can deal with multiple threats in parallel. Often human error and negligence can create security challenges, but the self-learning abilities of AI can nullify such mishaps.
Minimize Redundant Processes
Often monitoring cybersecurity alerts can become a monotonous and repetitive task which can make human experts go complacent or even experience “alert- fatigue”. AI-enabled automation can free resources from mundane tasks and perform a comprehensive analysis of day-to-day activities to fix potential security pitfalls.
Also, AI-based cybersecurity mechanism accelerates the overall incident detection and response time saving your IT resources from irreversible damage.
AI-enabled Multi-level Authentication
User login to websites or sharing personal information via online forms deals with sensitive information. AI-enabled cybersecurity mechanism offers a wide array of multi-level authentication like CAPTCHA, face recognition, and other biometrics so that fraudulent login attempts are detected and thwarted.
AI-enabled Combat against Bots
Often hackers use Bots to spread malware and steal data. AI tools are capable of identifying and blocking harmful bots as they can identify patterns and deploy honeypots to catch them.
The Rise of AI Threats and Cybersecurity Predictions for 2024
AI can be a double-edged sword, as hackers and malicious users can get access to AI-powered tools and can come up with novel AI-powered cyber threats.
Research says a hypothetical AI-powered cyber threat comprises the steps depicted in the following block diagram:
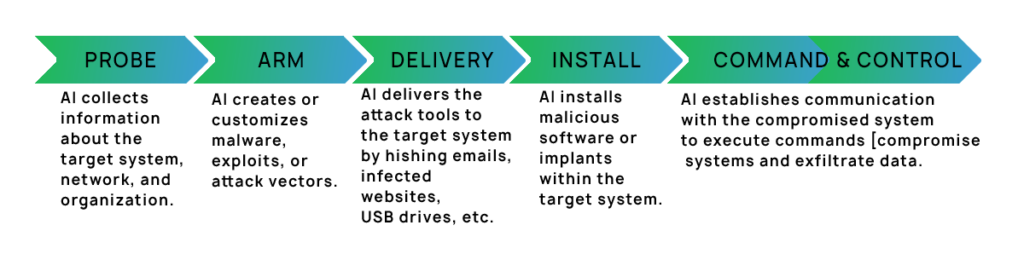
The above block diagram illustrates the ill effects of what is termed Shadow-AI, a situation where employees use publicly available Generative AI tools to enhance productivity. Therefore, they put organizational intellectual property and sensitive information at risk.
The impact of AI in cybersecurity is beyond skill empowerment. AI-driven systems exhibit real-time adaptability and contextual decision-making abilities thus boosting the productivity of organizations.
AI in cybersecurity offers significant benefits like detecting novel threats, handling voluminous data, and automating redundant tasks. However, it’s a double-edged sword as adversaries also leverage AI for cyberattacks. The future of threat intelligence lies in robust AI-driven solutions that enhance security while countering evolving threats. Balancing AI’s potential with its risks is crucial for building resilient cybersecurity infrastructures.



